|
| Building Own SIEM Environment using Opensource Tools (PART 1) |
What is a SIEM?
Security Information and Event Management are systems collect data from a variety of sensors, perform pattern matching and correlation of events, generate alerts, and provide dashboards that enable analysts to see the state of the Servers, Systems and Networks.
Before we discuss further, What is a Security Operations Center (SOC)?
Security Operation Center (SOC) is a centralized function within an organization, which monitor, detect, prevent, investigate, inform, respond to cyber threats and security 24/7. SOC working as central command post, taking automatic action & measurement on an organization's IT infrastructure, including its networks, devices, appliances, and information stores, wherever those assets reside.
SOC is the correlation point for every event, which logged with in organization and its also monitor and decide it. how they will be managed and action on them. As the implementation component of an organization's overall cybersecurity framework, security operations teams act as the central point of collaboration in coordinated efforts to monitor, assess, and defend against cyberattacks.
SOCs have been built around a central architecture, Where we implemented a variety of systems, such as Security Information & Event Management (SIEM), vulnerability assessment solutions (VAS), governance, risk and compliance (GRC) systems, application and database scanners (ADS), intrusion prevention systems (IPS), user and entity behavior analytics (UEBA), endpoint detection and remediation (EDR), and threat intelligence platforms (TIP).
SIEM system require well-written rule sets for process data. Every SIEM system may also have own query language, enabling us to write detailed, complex query sets so we can further automate data transformation and analysis actions. Every SIEM System has some of following particulars,

Dashboard:- The SIEM dashboard is the central nerve center of a security analysis tool for a cybersecurity analyst. It presents all the information the analyst needs to know, at their fingertips, as well as provides the interface to managing the different data that can be manipulated and viewed. Analysts can create queries, execute them, and view the results from the dashboard, as well as manage the different functions and options of the analysis software itself. This makes using the tool much simpler, more efficient, and effective.
Rule and Query Writing: All network devices, whether routers, firewalls, intrusion detection/prevention systems, or SIEM systems, have their own built-in rulesets and queries. Rulesets are typically found in network devices that actually take action, such as routers and firewalls. Queries are more often found in more advanced devices where you need to analyze information coming from those devices, such as an IDS or SIEM system. Most popular SIEM systems, such as Splunk and the Elasticsearch, Logstash, Kibana (ELK) open-source system, have their own unique rule and query languages. Splunk has the Search Processing Language (SPL), while ELK uses its Kibana Query Language (KQL). Many SIEM systems have the ability to import rules and queries created in other language. Queries can be very simple or quite complex, depending on what type of specific data you are looking for, the volume of data stores you must search through, and the complexity of the criteria you are imposing on the search. One of the key elements of a query is the string search. Queries can look for characteristics of certain data elements, such as an IP address, that are frequently found in defined fields. Typical search parameters for queries include the following
- IP or MAC addresses
- Domain names
- TCP/UDP port
- Protocol
- Traffic classified as allowed, denied, or dropped
- Username
- Dates and Times
- FileName
- File Size & Contents
- Bandwidth usage or volume of traffic
- Action (for example, account creation, file deletion, or website accessed)
- Inbound versus outbound traffic
Why we need SIEM ?
Next question in your mind is why we need SIEM ? IT teams perform daily basis task. But organization has no centrally view of what IT team do daily basis. Following are some reason Why we need SIEM,
- Compliance:- You know that every organization follow some rules and regulations for long survival in the market. It's very tough for every organization to follows security procedure to handle them individually. SIEM can easily handle them directly or indirectly. Such as PCI-DSS, GDPR, HIPPA, SOX, and other compliance standards.
- Operation Support:- You know that every organization give support to end users. Organization size increase day by day and its difficult to give to mange all services of NOC and SOC. But when any threat or intrusion happens then all of our users have to suffer. But when you are using SIEM then it collects all your data from different sources and stores them in one place. Then that data is managed, monitor and scan by a team of specialists. So you can easily give support to end users on security, threat and intrusions.
- Zero Day Threat:- zero-day exploit (also called a zero-day threat) is an attack that takes advantage of a security vulnerability that does not have a fix in place. Three are many solutions that are
available in the market do not equip us with zero-day threat detection. SIEM solution provides you zero threat detection system technique and you can trust a SIEM for your business safety and security.
- Advance Persistent Threats:- You know that advanced persistent threat (APT) is a broad term used to describe an attack campaign in which an intruder, or team of intruders, establishes an illicit, long-term presence on a network in order to mine highly sensitive data. Security team is not successful to provide a depth security and they are not capable of handling that much data and activities of your business. But using SIEM technology, its bring centrally operation engine, where you can perform all your task, such as monitor, detection, investigate and scanning etc..
- Investigation and Forensic:- You know that the forensic investigation is a long-term process. And that investigation also demands old data of the business to solve any kind of case regarding your business. Normal business security doesn't have enough strength to handle that much data in its storage. But SIEM provides you a large data storage option which you can use for storing data and you can show it to others very well.
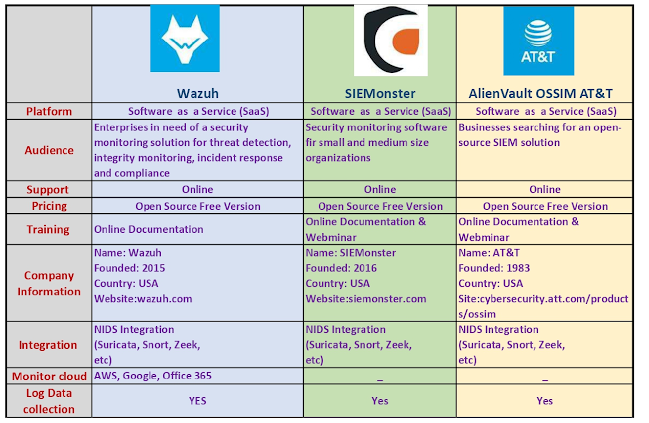
In Part 2, we discuss further on SIEM and we are going to build 2 different open source SIEM .If you have any question, you can ask me in comments section and follow my blogs for cyber security tools and discussion.
.jpg)













.jpg)